
CCNY Tech provides a wide range of ITAD services. We serve customers in a variety of ways, throughout the lifecycle of their equipment. For some companies, we perform “cradle to grave” type services. We begin with the delivery and installation of IT equipment, we maintain it throughout its use, and we decommission and remove it at the end. The process ends in remarketing or recycling retired assets, and once again supplying new equipment or upgrades.
The 6 Step Process of ITAD Services at CCNY Tech
fReceive, Tag, and Inventory Devices

Receiving – CCNY Tech will receive and record invoice information, model, configuration, MAC address (wired and Wi-Fi), and serial number into inventory spreadsheets.

Asset Tagging – CCNY Tech will remove each asset from its packaging and place an asset tag physically on the device. CCNY will also record asset numbers on the outside of device packaging.

Repack and Storage – CCNY Tech will re-pack and place device into inventory as “Ready for Deployment” and will store the asset in a designated client inventory locked cage on-site.

Transport – CCNY Tech will deliver the “Ready for Deployment” asset per the client’s request during the hours of 9AM to 5PM, Monday through Friday. Minimum of 10 devices per delivery.

Processing of Retired Assets
Refurbished Asset – CCNY will pick up retired assets per client request and fully refurbish for resale or process as E-waste if there is no resale value. All client information will be removed from each device and a DOD wipe of any hard drives will be performed.

Remarket Retired Asset – CCNY Tech will remarket assets to our customer user base to maximize returns. Each device will be processed for reuse or recycling, and all profits split with the client. As each asset is sold it will be added to a Purchase Order Report. Monies due to the client will be paid on a monthly basis with all accounts being settled up by the end of each calendar year.
If your company or organization are looking to upgrade or decommission servers, storage or networking equipment, CCNY Tech has the best solution to keep your data secure, help the environment, and perhaps make you some cash for your “no longer needed” IT gear. Give us a call at 1-800-566-4786 and speak to an IT specialist about IT Asset Disposition Services from CCNY Tech.
By Ron Pasquarelli

CCNY Tech has a variety of products from some of the top names in the industry! We supply servers, networking, and storage equipment, along with custom configurations. Check out our site or call our team to learn more about our products and services! Visit Website


 While there are many important aspects of
While there are many important aspects of  When a device has outlived its usefulness, the next step is to send it off for recycling. But, what if this device still contains sensitive data? How do you assure that wherever this drive ends up, your data will not be going with it?
When a device has outlived its usefulness, the next step is to send it off for recycling. But, what if this device still contains sensitive data? How do you assure that wherever this drive ends up, your data will not be going with it?
 The
The  The
The 
 Leasing helps to prevent technological obsolescence. Because technology is constantly changing, it is easy for equipment to become outdated.
Leasing helps to prevent technological obsolescence. Because technology is constantly changing, it is easy for equipment to become outdated.

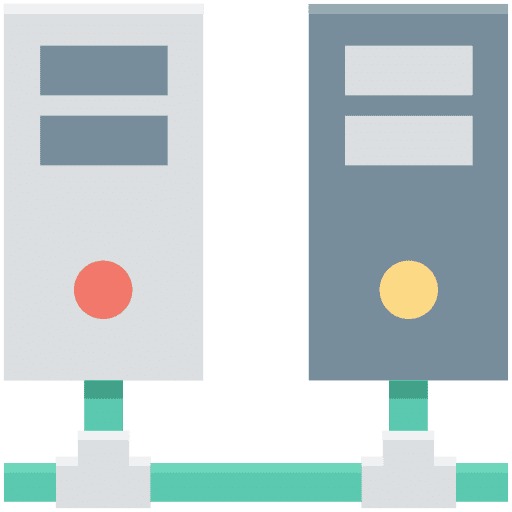 What are the benefits of an in house server?
What are the benefits of an in house server?
 On Saturday March 4th, members of CCNY Tech’s sales team – Matt Skinner, Chris Baris and Joe Coffay participated in the 43rd annual America’s Greatest Heart Run and Walk. The guys braved frigid race time conditions and completed the 5 mile run in what they claim was a “respectable”, but still yet to be revealed time.
On Saturday March 4th, members of CCNY Tech’s sales team – Matt Skinner, Chris Baris and Joe Coffay participated in the 43rd annual America’s Greatest Heart Run and Walk. The guys braved frigid race time conditions and completed the 5 mile run in what they claim was a “respectable”, but still yet to be revealed time. or!
or!
 When licensing a physical server of 16 or fewer cores, you purchase a 16 core pack version of Windows Server 2016, regardless of the number of physical CPUs. With 2012 R2 however, the amount purchased was based upon the number of physical CPUs to be licensed, regardless of core count.
When licensing a physical server of 16 or fewer cores, you purchase a 16 core pack version of Windows Server 2016, regardless of the number of physical CPUs. With 2012 R2 however, the amount purchased was based upon the number of physical CPUs to be licensed, regardless of core count.
 1. Catch it at the beginning.
1. Catch it at the beginning. CCNY Tech is a leader in
CCNY Tech is a leader in 
